SASE and SSE: Strengthening Enterprise Security in Hybrid Environments
The changing business environment has made it more critical for organizations to adopt flexible, i.e., hybrid or remote, working models. These changes enhance productivity and retain and attract talent; however, they also introduce certain challenges, such as reworking the traditional security perimeter, which enterprises must mitigate. Why? Primarily because employees access corporate resources from various locations, devices, and networks, this makes the data, and thereby the company, vulnerable to attacks or breaches that traditional, on-premise security measures cannot protect.
Simply put, the once-clear boundary between the internal network and the public internet has dissolved, making it a critical necessity to rethink how to secure the modern, evolving enterprise. This is where Secure Access Service Edge (SASE) and its fundamental building block, Security Service Edge (SSE), can help companies.
The Legacy of "Castle-and-Moat" and the Birth of SASE
When remote work wasn’t the norm, enterprise security relied on a "castle-and-moat" model, meaning that no one outside the network could access the data, which was protected by firewalls and other on-premise appliances. Basically, only users and devices within the corporate network were allowed. But because of the changing business model, this is no longer sustainable. It slows down connections and makes apps frustrating to use. More crucially, it is opening up security vulnerabilities, as remote workers don't have traditional perimeter-based network rather a direct access to cloud services from home or a coffee shop. So, managing different security tools—like a firewall and a separate VPN— becomes complicated for IT teams and makes the company's security weaker.
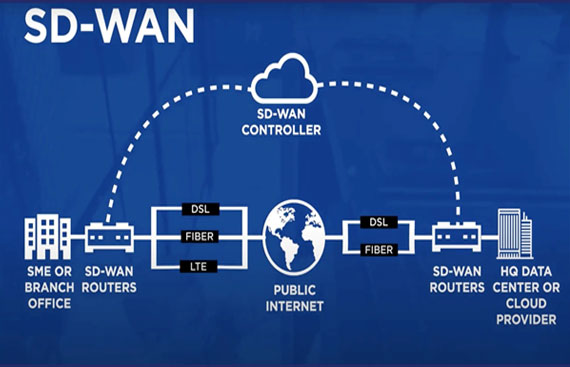
“However, this evolution has also introduced a new solution: SASE, a term coined by Gartner. It addresses these challenges by unifying networking and security functions into a single, cloud-delivered cyber security solutions. An end-to-end SASE solution natively converges features such as Software-Defined Wide Area Network (SD-WAN), Cloud Access Security Broker (CASB), Secure Web Gateway (SWG), and Zero Trust Network Access (ZTNA) into one integrated platform. This single-vendor paradigm makes management easier, enforces consistent policy across all, and offers a single view of the entire network and security infrastructure.
Understanding Security Service Edge (SSE)
At the heart of any SASE framework is SSE, which represents the security-focused subset. SSE provides all of the critical security services minus the networking aspects, such as SD-WAN. It's designed specifically to protect user access to the web, cloud, and private applications and enforce policies and inspect traffic at the edge, near the user. A robust SASE solution employs SSE to secure all the connections regardless of the user's location. The following are the most critical elements of SSE, which are critical in fulfilling this mandate:
Zero Trust Network Access (ZTNA)
Whereas legacy VPNs grant general network access, ZTNA is built on the "never trust, always verify" model. It delivers identity-based, secure access to individual private apps on a "least privilege" model. Each request for access is authenticated individually, allowing users to receive only the access they absolutely require.
Cloud Access Security Broker (CASB)
More and more companies utilize more and more cloud applications, and CASB assists them in discovering and managing approved and unapproved cloud applications. It protects against data leakage through monitoring data traffic and enforcing security policies on different cloud infrastructures.
Secure Web Gateway (SWG)
The SWG feature protects users against web-borne attacks, such as malware, phishing, and malicious URLs. It scans web traffic and applies company policies to provide a secure browsing experience for all employees, either in the office or remotely.
A next-generation SASE solution, like one from Tata Communications, makes a zero-trust security model possible, where each request for access is authenticated. The strength of these solutions is that they can simplify complexity, increase visibility, and improve security throughout the entire enterprise so that companies can securely scale while they protect their distributed workforce.
